Instructions for using the ELIXIR-SI infrastructure
SFTP
For access, use any program that knows the SFTP protocol. Computers with OS linux or Mac already have programs for this (e.g. scp), on Windows OS you need to install the appropriate program.
OS Windows:
- We recommend the free WinSCP program.
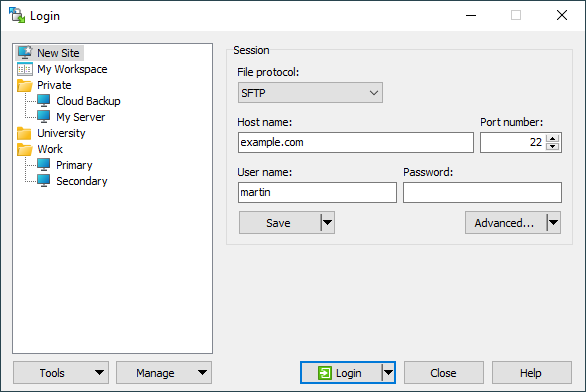
- Open the WinSCP program and enter the data you received via e-mail in the window and click Login:
- Host name,
- Port number,
- User name,
- Password
- When you log in for the first time, the system will ask you to change your password. Set an appropriately secure password.
In the archive, you can access your home folder, which is located in the home (/home) folder. Your home folder name is the same as your username.
If you experience any further challenges with access, please contact your local system engineers administrators for assistance.
SSH access – access to SLURM
SSH clients
You can use any standards-compliant SSH program / client of your choice for access.
Some clients:
Rules on the use of research ICT (RIKT) ELIXIR-SI infrastructure
Users must follow the following policy on the use of RIKT ELIXIR-SI:
Terms and conditions
- The user uses the systems and services in accordance with the stated goals and job description on the basis of which he gained access.
- The user observes the rules on acceptable use of the ARNES network and the Academic and Research Network of Slovenia.
- The user may not use the services and systems for purposes that conflict with the applicable legislation of the Republic of Slovenia or the European Union, including legislation on the protection of intellectual property and confidentiality agreements.
- Users undertake to use only software with valid licenses for use on the system.
- The user uses the services at his own risk. The user accepts that the service provider does not guarantee the availability of the services at a certain time and does not guarantee the usability of the services for a certain purpose.
Security terms
- The user is responsible for the security of his software, his data and his access credentials, such as passwords and private keys.
- The user will not (attempt to) bypass or disable administrative or security restrictions.
- The user will not try to negatively influence the functions of systems and networks and will not intentionally interfere with or disable the use of other users of the system.
- The user will not access the data of other users and will not change, unseal or delete it.
- The user will notify RIKT administrators/system administrators without delay of any found or suspected security breach, accidental access to data or other inappropriate use of systems and access credentials. The official contact of the RIKT administrators is elixir@mf.uni-lj.si.
- The user agrees that he is responsible for the security of his data, including establishing appropriate security restrictions and permissions, using an appropriate data storage location, and using encryption where appropriate.
Personal data, limitations of identification and data policy
- The user agrees that access to the system is exclusively his personal access, obtained in his own name and may only be used by the owner himself.
- The user is obliged to ensure that the information about the user in the system is correct and up-to-date. The user does not use false or misleading personal information when using services that require personal information.
- The user will not allow third parties to use their account and will not intentionally or due to carelessness and negligence allow third parties access to the system, nor will they attempt to gain access to the account of other users.
- The user agrees that data will be stored in the system, including registration data, security data, accounting data and administrative data, and expressly allows the use of data for operational purposes, accounting purposes, monitoring purposes, security and administrative purposes. The user also agrees to keep the data until the end of the accounting year after the termination of the access right or after the last access to the system, unless otherwise agreed.
Obligations to the administrators of RIKT ELIXIR-SI
- The user agrees that RIKT administrators/system administrators have access to his software, data and information and that they may monitor network traffic for the purpose of performing security checks and monitoring usage.
- The user agrees that RIKT administrators/system administrators have the right to manage, freeze or terminate access rights within their scope of work, and that they will follow their instructions without delay.
- The user agrees to provide RIKT administrators/system administrators with information about system usage and the results of their work for the purposes of reporting and informing the public about the use of public resources.
- The user agrees to provide adequate indication of the use of RIKT ELIXIR-SI or citations for used resources and services in accordance with the requirements of RIKT administrators and as indicated on the ELIXIR-SI website (https://elixir-slovenia.org/about-us/acknowledge-elixir-si-funding-and-support/).
Data management
Data backup
In the ELIXIR-SI information system, there are currently no real backup copies of user data. All users are responsible for their data.
Data cleaning
The home folder (in /home/<user>) on RIKT ELIXIR-SI servers is permanent memory with a default capacity of 1 TB. For a larger amount of data, it is necessary to agree individually.
Other data beyond the agreed amount is considered temporary and will be deleted.
Usage costs
The costs of using the equipment depend on the specifics of each research study and are agreed upon with each user individually. Basically, the costs consist of research infrastructure management costs and equipment costs.
We charge all services on a non-profit basis. For the first cooperation, we charge for the working hours spent and any material. For long-term cooperation, the optimal form of cooperation is a partnership in a research project, where we also cooperate in terms of content.




